Alien Crypter
C++ | .NET | RT & ST
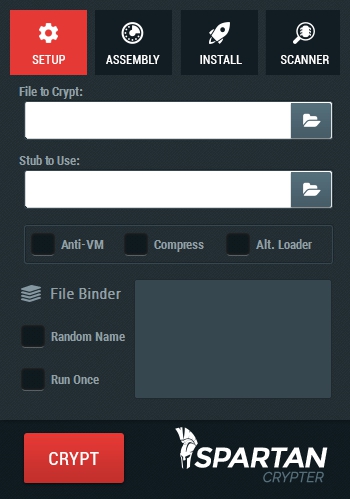
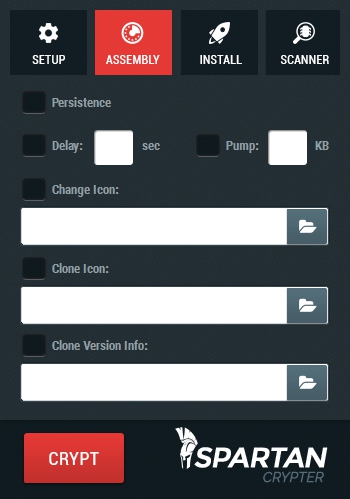
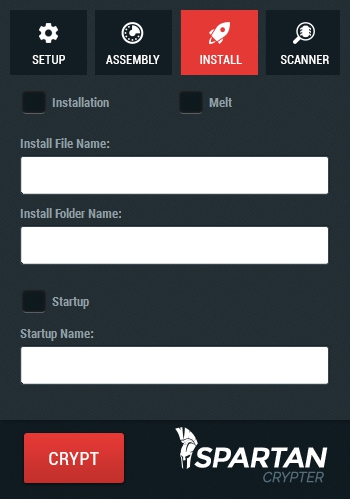
Alien Crypter isn’t your average rundown crypter with completely useless features, we only give our clients what they truly need, a functioning crypter that is constantly updated and is always available when you need it, all with the essential features needed.
Order Now